As part of the Network Services room in TryHackMe, one of the areas covered is NFS. I will cover the…
Learning
As part of learning about Telnet in TryHackMe we practiced some methods in which FTP can be exploited. I have…
Definitions Evil Twin Access point which looks like a legitimate access point but is actually maliciousOften copies SSID Rogue Access…
Malware A blanker term for software that is specifically designed to disrupt, damage, or gain unauthorized access to a computer system….
Hi all, this is a dictionary page! SYO-601 covers a lot of content in a fairly shallow manner. Rather than…
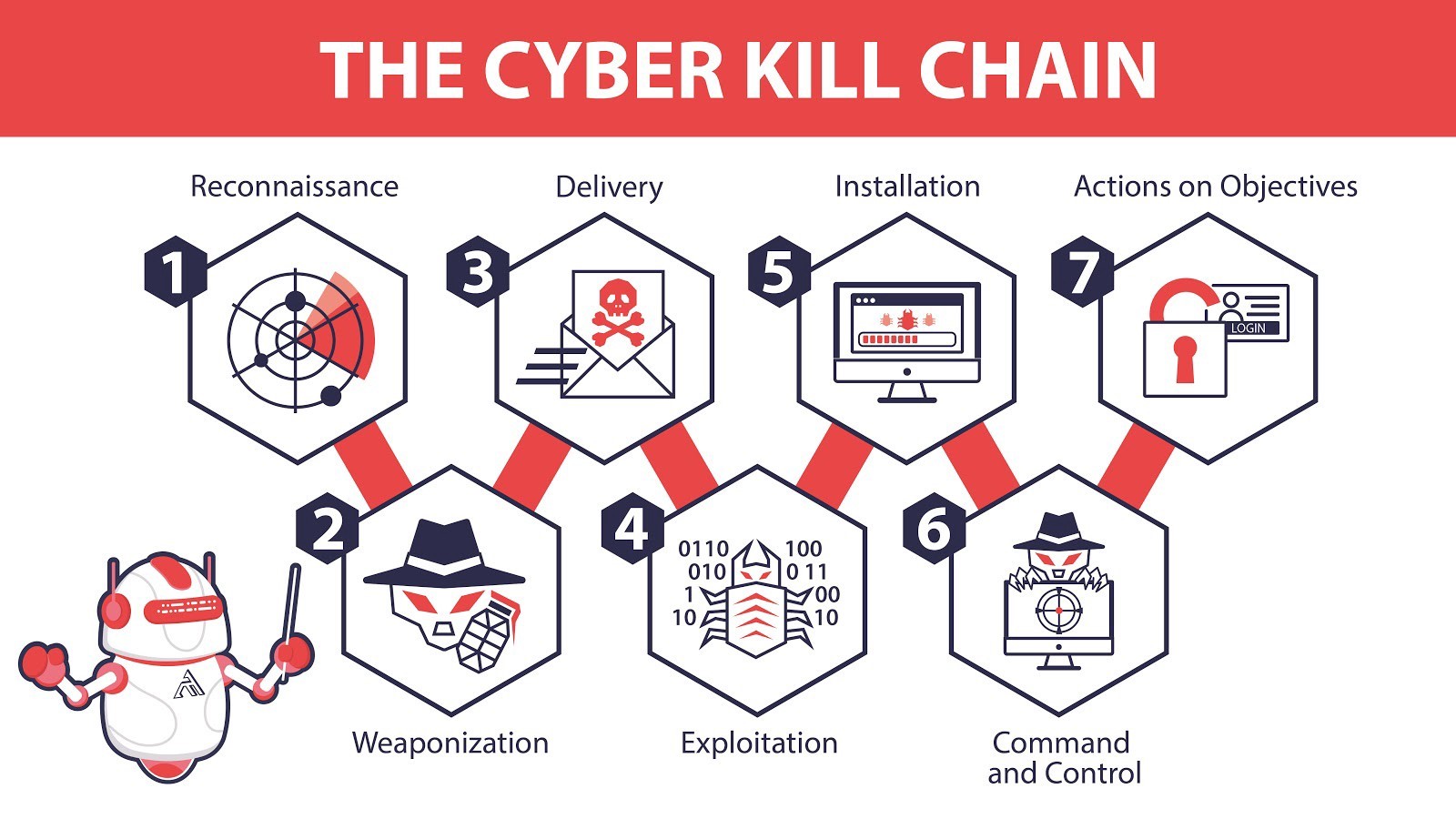
Welcome to Day 2. today we’re covering the Cyber Kill Chain. The Cyber Kill Chain is an attack framework is…
Notes from Security 601+ – Module 1.5 threat intelligence is an essential tool for cyber security practitioners. While it’s all…
Hello everyone Welcome to my 1st knowledge post! We’ve adopted kittens this week so it is pretty manic here in…