Understand the Cyber Kill Chain
Welcome to Day 2. today we’re covering the Cyber Kill Chain.
The Cyber Kill Chain is an attack framework is a framework created by Lockheed Martin in 2011. It is an adaptation of an existing military concept. While far from perfect as the security world has developed significantly in the past 10 years it’s an important concept to be familiar with in the profession.

What is it for?
The purpose of the Cyber Kill Chain is to help understand against ransomware attacks, security breaches in addition to APTs. It’s also useful as a way to assess the current network to identify security gaps.
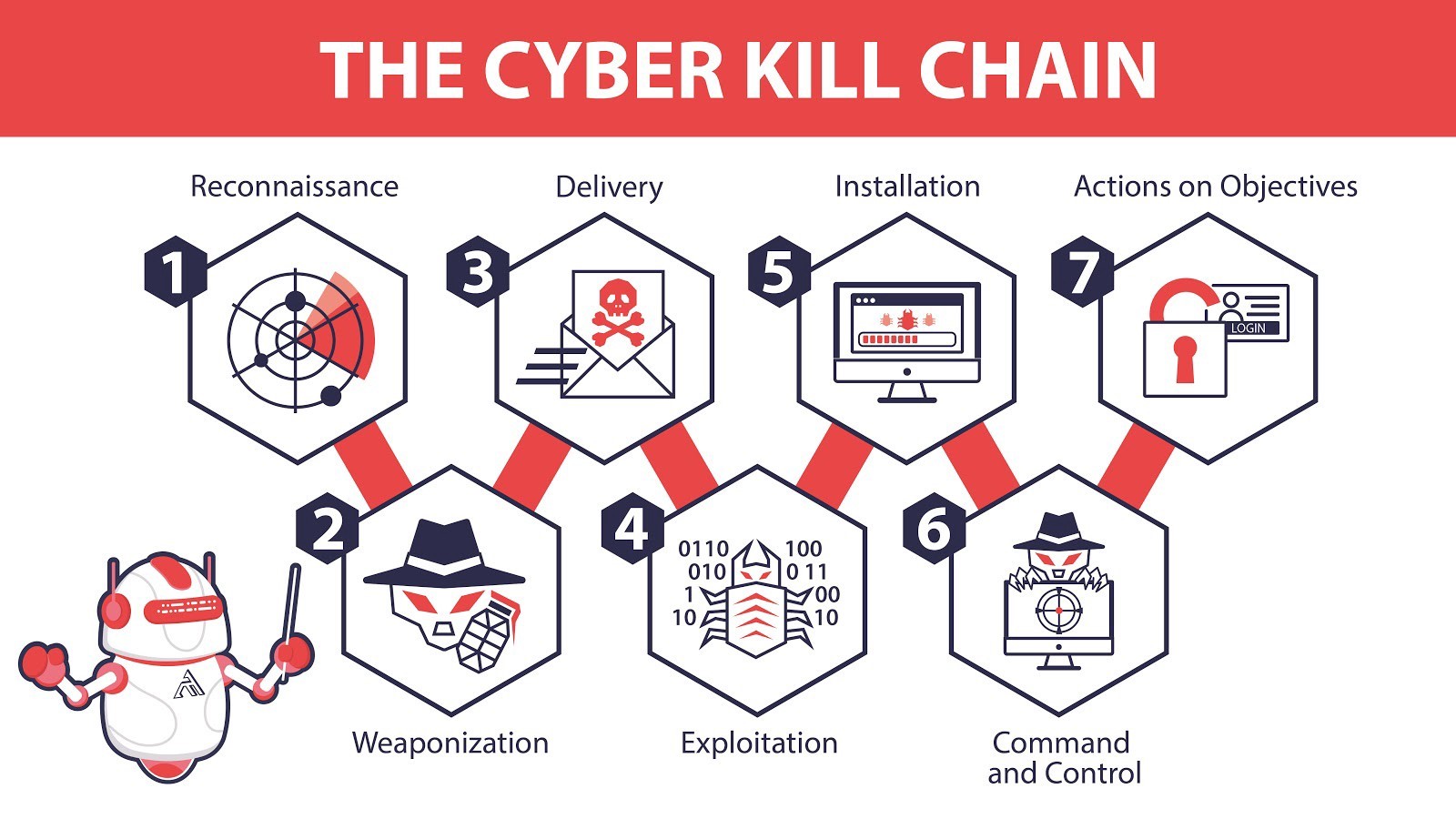
The stages in the Cyber Kill Chain are:
- Reconnaissance
- Weaponisation
- Delivery
- Explotation
- Installation
- Command & Control
- Actions on Objectives
Reconnaissance
This stage involves discovering and collecting informaton on systems/victims. This is a PLANNING stage. The various intelligence gathering types covered HERE (tbw) are covered in this stage.
Weaponisation
After completing the reconnaissance stage the next is to build the tool. This is the malware or finding the exploit which will be used to deliver the payload to the victim. The tool would usually either be built using an automated tool or bought from the Darkweb.
Some common ‘weapons’ are: Macros, VBA scripts, payload, worm, trojan, virus, backdoor, rootkit etc
Delivery
The delivery phase is the decision on the method of delivering the payload/malware to the victim.
Examples of this are: Watering hole attacks, injected USB sticks, phishing emails
Explotation
Now the attacker has decided the weapon and executed the delivery they now need to exploit the vulnerability created. They use lateral movement to gain further access to the machine.
Installation
This stage handles re-entry if/when the attacker wishes to re-access the system either to further attack or to continue transfering protected data.
To do so the attacker would perform a ‘persistent backdoor’ and is alternatively referred to as an access point. Some methods are:
- Installing a web shell on a webserver.
- Installing a backdoor on the victims machine
- Creating/modifying a Windows service using T1543.003 (see MITRE ATT&CK matrix).
- Adding run keys to the registry to launch the malicious payload
Attacker can also use Timestomping to help prevent detection.
Command & Control
Command an Control is the stage where the installed malware on the victims machine is accessed via a Command and Control (C2) communications channel to control and manipulate the infected machine. This is commonly termed C2 Beaconin or C&C.
Common examples of C2 channels are:
- Using TCP80 and TCP443 (HTTP & HTTPS). This is a form of hiding in plain sight and allows traffic to hide within legitimate traffic.
- Using constant requests to the DNS server that belongs to the attacker as a method to transport data. This is also known as DNS Tunneling
This is a topic which deserves a lot more information that has been given here. A good site found for some of the intricacies can be found from Palo Alto.

Actions on Objectives (Exfiltration)
With the previous 7 steps done the hard bit is done. The attacker has undetected access to the system and can work on navigating the internal network to achieve their goals. Some of the possible actions they could take are:
- Credential harvesting
- Privlidge Escalation
- Internal Reconnaissance (interacting with software to find more vulnerabilities!)
- Lateral movement
- Collect/Exfiltrate sensitive data
- Deleting essential backups &* shadow copies
- Data overwriting / corruption


