A brief summary of the Pyramid of Pain
Hello everyone
Welcome to my 1st knowledge post!
We’ve adopted kittens this week so it is pretty manic here in the Raine/Ford household (obligatory cat photo at the end for you attentive readers).
As a starting point I’ve been working through tryhackme. It’ been a great resource to learn and get some of specifics I’ve been missing.
So today, not ominous at all is the pyramid of pain!
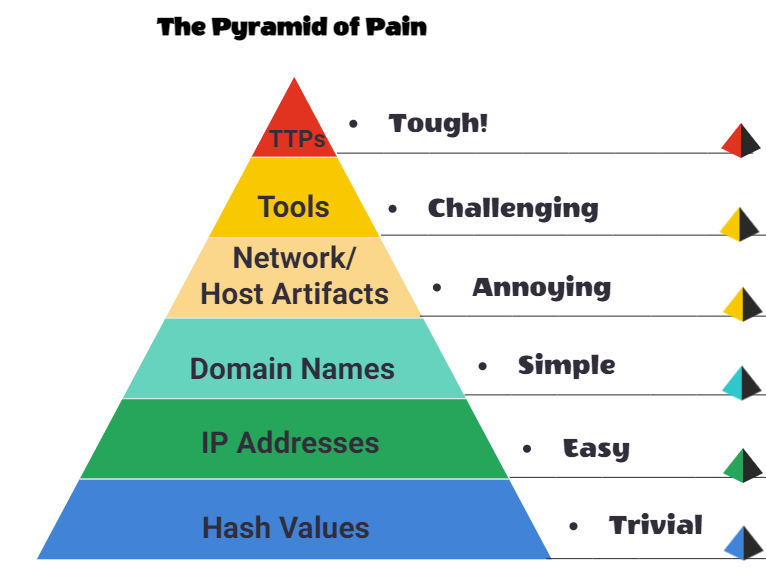
The Pyramid of pain is as follows:
Hash Values
Hash values make an easy source of attack for an improperly defended network. Using hashing methods such as MD5, SHA-1 and SHA-2 all provide points of failure as small modifications can cause simple hash awareness to miss this. Methods such as a IDS can be used to protest against this by comparing similarity and on-the-fly lookup of hash values against known values.
Security professionals can do hashlookups by visiting sites such as virustotal.com or metadefencer.opswat.com
This type of attack is the perhaps the easiest for an attacker to target and modify as it involves very little effort to modify a hash and try again.
A common defence method against this is called Fuzzy Hashing a analysis algorithm which detects similar hashes and can be incorporated into Detection/YARA rules to seek out malcious hashes. One way Fuzzy hashing is utilised is with SSDeep.
IP Addresses
IP addresses ae perhaps a little harder but still an easily modified vector of attack. Any defended network with have realtime IP analysis alongside a list of blocked IP addresses used to identify malicious attackers. If a defender were to detect and block a certain IP it is easy enough for an attacker to modify the IP to avoid these checks.
A common technique used by botnets to attempt to circumvent network protection is to use Fast Flux. This uses a large number of infected hosts as proxies which allow for the central Command and Control Server to remain hidden. While this technique is by no means fool proof it does add complexity to the defence.
Domain Names
This vector of attack is easier still to protect against and perhaps less common due to the additional cost of purchasing replacement domains.
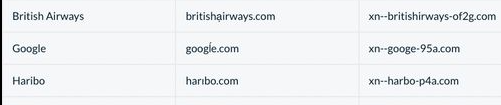
A common method of phishing using domain names is by utlising Punycode. Punycode is a way of representing unicode within ASCII which is used with domain names. This makes it difficult for the unwary eye to spot the difference.
Network Artifacts
Network artifacts are more difficult on both sides. This becomes more like your traditional cat and mouse game as Jerry (hopefully) defeats Tom and Tom goes off to plan another elaborate way of catching that mouse.
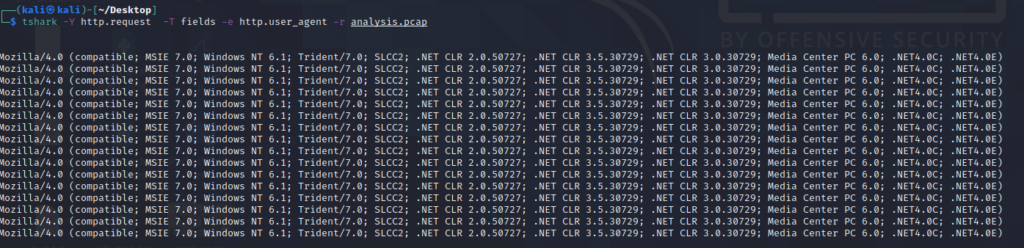
A network artifact can be a user-agent string, C2 information or URL pattern followed by a HTTP post request. Security defenders use tools such as Wireshark compared with protocol analysers like Tshark or by using IDS to combat the threats.

Tools
Tools is getting the tricky stage now. The network is secure from the attackers threats and it looks like Jerry is winning! At this point Tom will go back to his workshop to come back with a new device to catch that mouse.
The considerations when the attacker needs a new tool is:
- Unless a totally different approach is gone for the tool will serve the same purpose just execute it differently.
- The tool will take time to create or at least cost the attacker money to use.
- The attacker may need to train giving the defenders more time.
The new tool will have it’s own binary signature and can be picked up by:
- Anti-virus signatures
- Detection rules
- YARA rules
Useful resources include MalwareBazarr and Malshare to help with this. The SOC Prime Threat Detection marketplace is a platform in which pre-build detection rules are shared and is kept largely up to date.
TTP
Finally but by no means less important is TTP. The definition of TTP is Tactics, Techniques and Procedures. This includes the MITRE ATT&CK Matrix and details the goals for protecting against numerous stages of an attack.
If you can follow the Matrix it leaves the attacker almost no chance of successfully compromising your security system.
That’s it for my first post. I’m aware the terminology isn’t quite as sharp as it should be but this is something I will improve at in the future. In the meantime thank you for reaching my quick summary of the Pyramid of Pain

