BTLO – Follina Challenge
Brief

Setup
Hardware: 1x Kali Virtual Machine
File Location: /home/kali/Desktop/Malware/FollinaChallenge/sample/sample.doc
Questions
Question 1) What is the SHA1 hash value of the sample? (Format: SHA1Hash) (1 points)
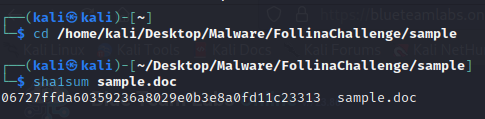
Answer: 06727ffda60359236a8029e0b3e8a0fd11c23313
Question 2) According to VirusTotal, what is the full filetype of the provided sample? (Format: X X X X) (1 points)
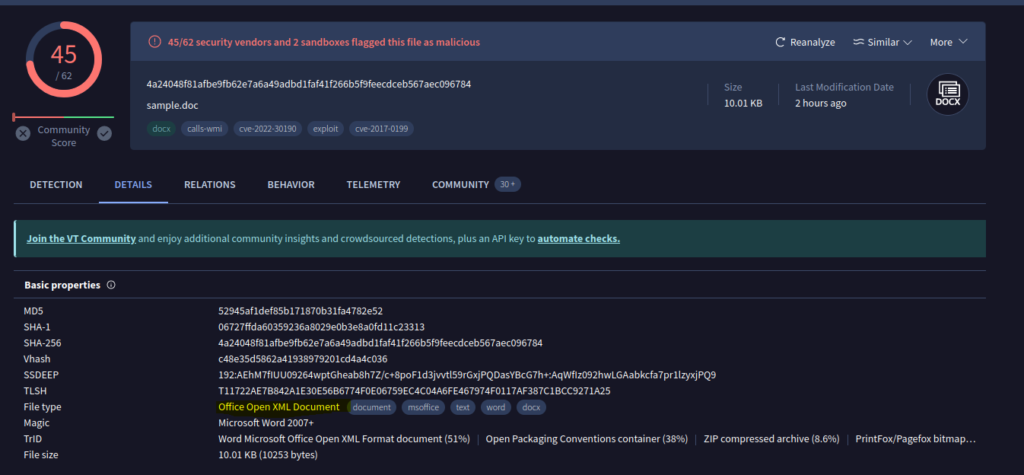
Answer: Open Office XML Document
Question 3) Extract the URL that is used within the sample and submit it (Format: https://x.domain.tld/path/to/something) (1 points)
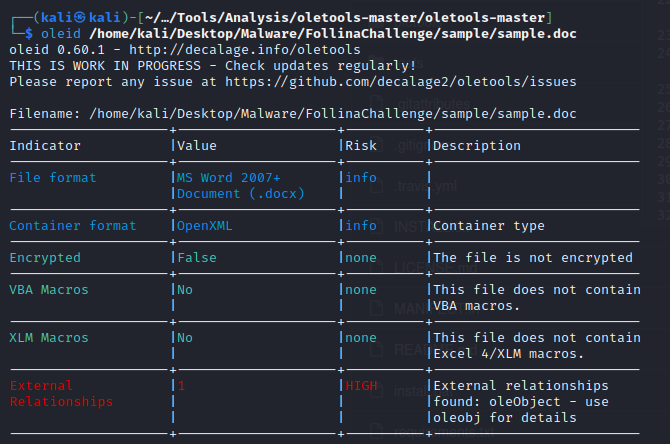
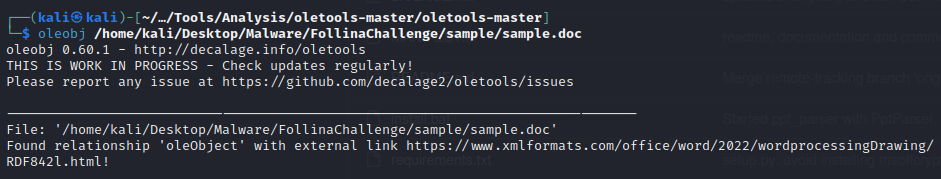
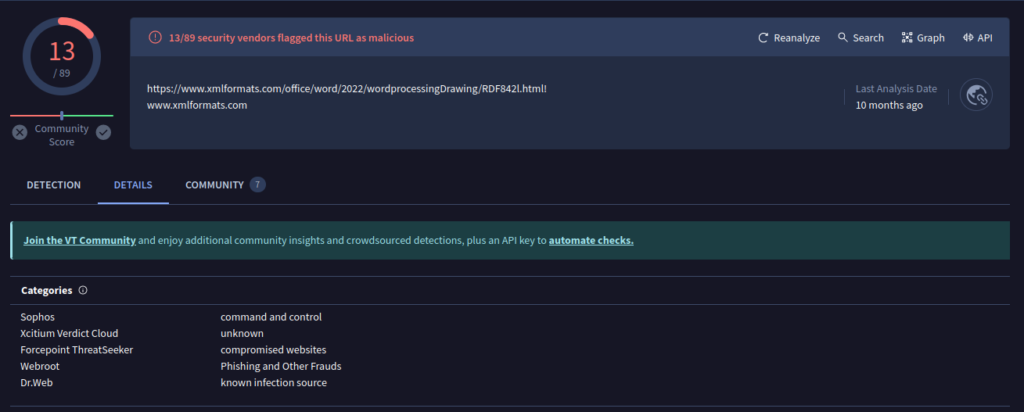
Question 4) What is the name of the XML file that is storing the extracted URL? (Format: file.name.ext) (1 points)
This question did admittedly stump me. I’m not overly familiar with the makeup of office files, however after doing some digging I learnt that the document file is made up of .XML files. This means it can be extracted! Once extracted the URL would be held within the .rels file.
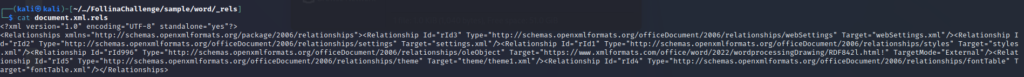
Question 5) The extracted URL accesses a HTML file that triggers the vulnerability to execute a malicious payload. According to the HTML processing functions, any files with fewer than <Number> bytes would not invoke the payload. Submit the <Number> (Format: Number of Bytes) (1 points)
Having attempted to run this in a sandbox, it appears that the domain no longer exists. Performing a NSLOOKUP confirms this
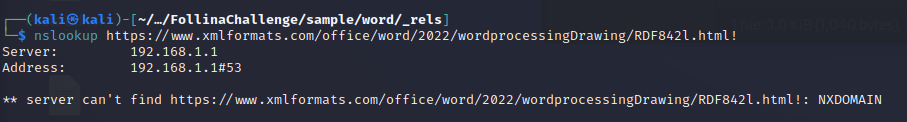
That’s disappointing but understandable, back to a little bit of OSINT, checking this URL we can see it’s related to CVE-2022-30190. Analysis done by Juniper shows that at least 4096 bytes is needed for the exploit to trigger.
Question 6) After execution, the sample will try to kill a process if it is already running. What is the name of this process? (Format: filename.ext) (1 points)
Again now we know the CVE finding information on this malware is easy. Secprod does a solid breakdown of the process and confirms that once the base64 is converted we get this:
Ok so from this we can see it’ll attempt to run taskkill to end msdt.exe.
Question 7) You were asked to write a process-based detection rule using Windows Event ID 4688. What would be the ProcessName and ParentProcessname used in this detection rule? [Hint: OSINT time!] (Format: ProcessName, ParentProcessName) (1 points)
Oh joy, more OSINT. Okay, so from my own notes I can see 4688 is process creation. The only obvious process we can see above is cmd.exe which in itself can be something of a worry but could also be used in legitimate use.
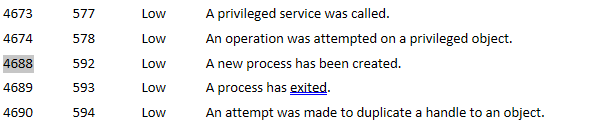
On the other hand we can see right at the end that it executed rgb.exe, however we do not know the parent process.
Through our OSINT efforts we can see that this malware will modify the msdt.exe so when it is re-created it will reopen in it’s tampered form. From a submission from Threatnix.io we can see that the parent process in this instance is winword.exe. Therefore the answer for this would be msdt.exe, WINWORD.exe
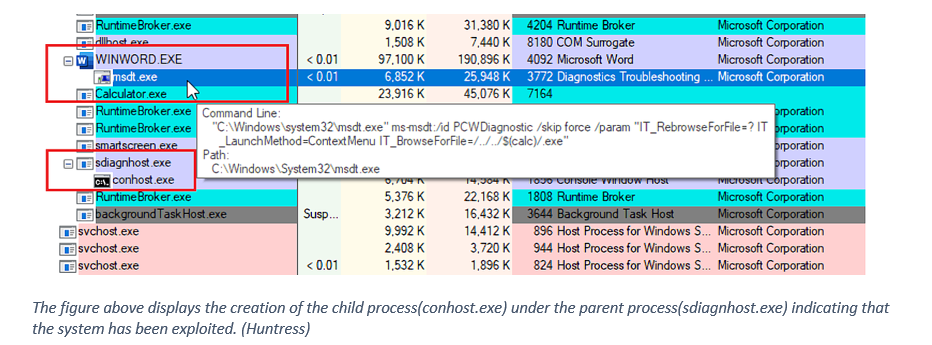
Question 8) Submit the MITRE technique ID used by the sample for Execution [Hint: Online sandbox platforms can help!] (Format: TXXXX) (1 points)
We’ve determined previously that this code executes via CMD, therefore looking at the ATT&CK Matrix we can see this falls under T1059
Question 9) Submit the CVE associated with the vulnerability that is being exploited (Format: CVE-XXXX-XXXXX) (2 points)
We already know from our previous research that the CVE is CVE-2022-30190.

Takeaway
- .doc files are made up of .xml files. These files can be extracted.
- Once extracted .rels contains metadata on the document


