Web App Vulnerabilities – Types and Safeguarding
As we move onto preparing for the CYSA+ 002 exam I am going to be reinforcing some of my learning by documenting them. Something which I have often struggled with is web attacks and how to recognise them. This is part of objective 1.3 of the Comptia CYSA+ exam.
Types of Web Attacks
There are a large variety of attacks, all of which are well documented. For the purpose of this article I will only be specifying those indicated on the CYSA+ exam objectives. Of these there are:
- XML Attack
- XSS Attack
- SQL Injection
- Directory Traversal
- Integer Overflow
- Session Highjacking
- Authentication Attacks (various)
XML Attacks
An Extensible Markup Language attack (XML) is a type of injection attack which occurs when an attacker can exploit how an application handles XML data.
What is XML?
The Extensible Markup language is a markup language which sets a series of rules for encoding documents which is both human readable and machine readable.
This language is commonly used in some AJAX applications, SAML authentication, in Javascript and APIs (SOAP).
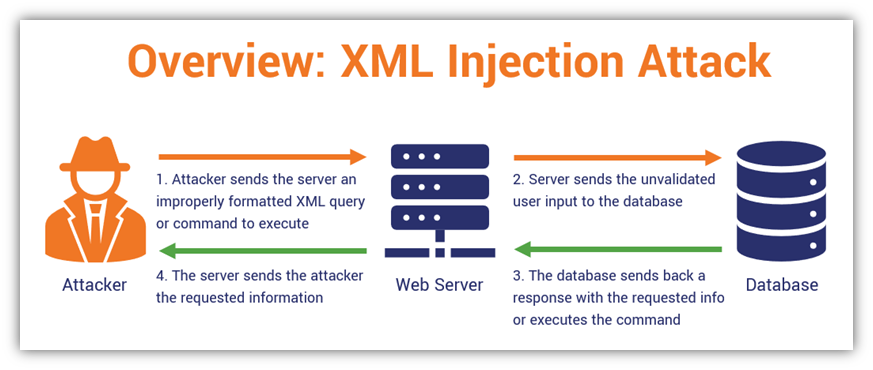
What is an XML attack?
An XML attack is an injection attack type against an application which can parse XML input. This is typically found on webapp data input fields but can be found on other types of applications.
If the XML input is allowed it can cause the XML Processor to divulge confidential information, result in DOS or pivoting to other internal systems.
Example Code Snippet
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<foo>&xxe;</foo>Safeguards
- This type of attack can be prevented using input validation. By disallowing the use of certain characters or phrases we can prevent unauthorised XML script being run.
- Disabled DTD. DTD or Data type Defintiion is a set of markup declarations which can be used to execute XML instructions. By disabling this from all relevant parsers you remove the ability for malicious code to run.
XSS Attacks
Cross Site Scripting is a input validation exploitation which can be used to run unauthorised code on a victims machine.
Unlikely other methods described here it often does not impact the server but instead targets users accessing server. This is done by injecting code into a trusted website by creating a URL holding malicious code. When the victim accesses the URL the malicious code gets read and executed by the client browser using the permissions provided to the browser.
Some examples of what an XSS attack can achieve is: accessing cookies, session tokens, other sensitive data held by the browser.
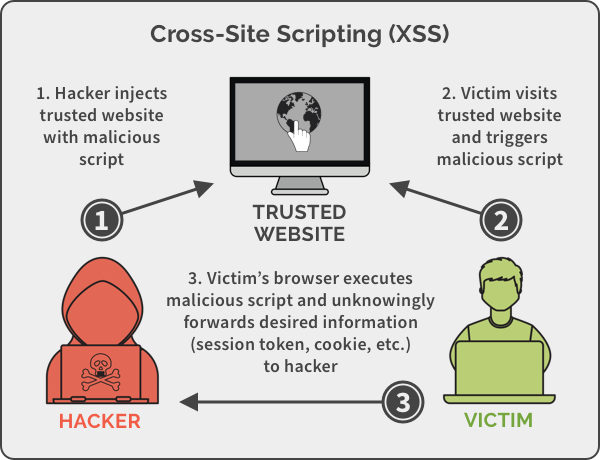
This attack is especially lethal as the end user could be following correct security best practices and still fall foul to an attack of this type.
There are a variety of XSS style attacks which can be reviewed here, however for brevity this will be covered in a later article.
Safeguards
- Turning off HTTP TRACE – This can lead to more data being vulnerable to XSS attacks.
- Proper output encoding – handling data so it is displayed exactly as the user has typed it and not allow it to be executed as code.
- HTML sanitisation – Using sanitisation tools can modify contents to strip HTML of dangerous variables.
- Safe Sinks – the method of nesting user inputs as strings rather than leaving them susceptible for execution.
SQL Injection
SQL injection is a common injection technique which proves a major security concern for database administrators.
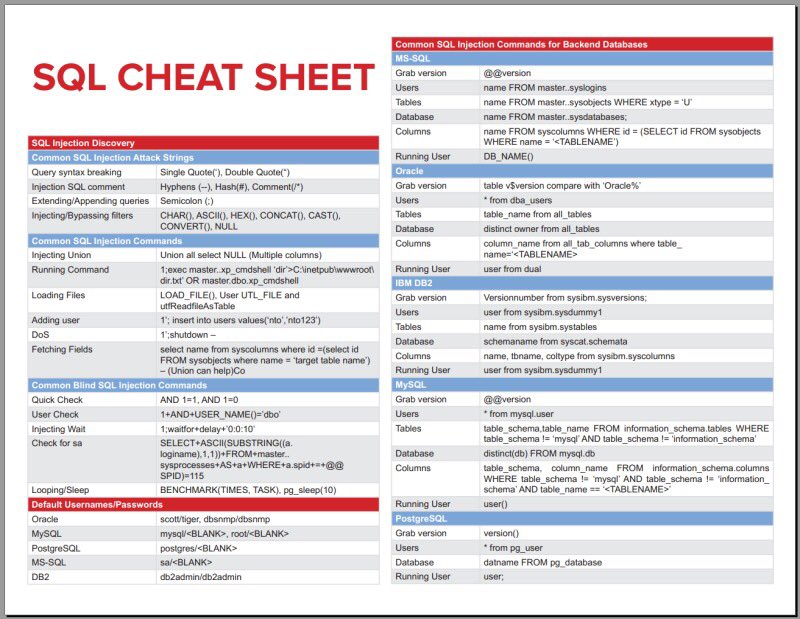
What is a SQL injection?
SQL is a database management tool developed by Microsoft. It is commonly used as a backbone server (a SQL Server) for company databases.
A SQL injection is a method for using improperly secured input fields to allow an attacker to directly communicate with a SQL server and make requests which can cause the manipulation of the server or the divulging of sensitive data held.
A SQL injection attack can usually be seen by seeing instances of 1=1 or SELECT * FROM
Safeguards
- Input validation – as mentioned previously input validation can prevent certain characters (*) or patterns from being submitted to the web server preventing attacks from running.
- Stored queries – SQL has the ability to create a selection of commands which can be executed using a single command. A good way to think of this is something similar to Macros. Forcing the use of these prevents unaudited commands from being executed.
- Least privilege – A common concept in IDAM but can also be used here. This is more of a compensating control, but by providing only the access needed by the executing account you can severely restrict the ability of the use account to executed any unauthorised commands.
Directory Traversal
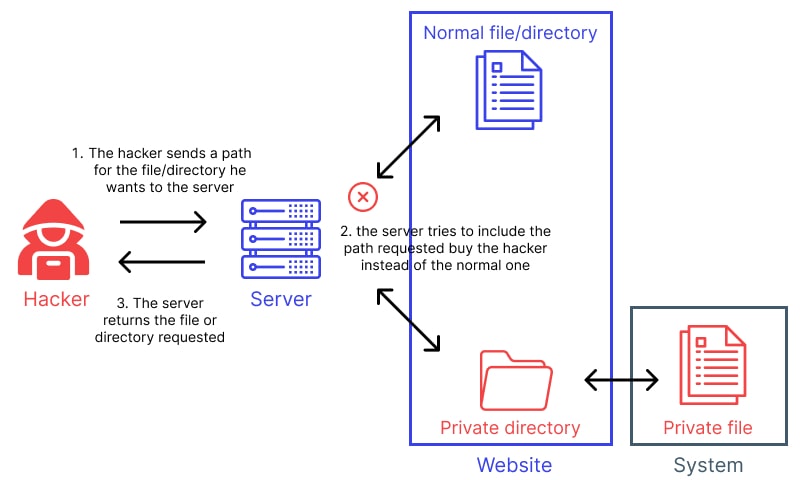
Directory traversal is a vulnerability which can be exploited to gain access to the local contents of a server.
When preparing for this attack an attacker can often gain details to the file structure of the server using loaded media within source HTML and then use direct or nested traversal sequences to navigate to the location of the server. This can be paired with other exploit tools to exfiltrate data from that source.
Safeguarding
- Input validation – starting to feel like a broken record, however preventing symbols such as % can prevent many directory paths from being specified.
- Storage location – a compensating control, you can reduce the impact of directory traversal by avoiding placing media within the server root.
- Configure the web API to restrict it’s directory access to a certain section of the directory
Session Highjacking
Session highjacking is an umbrella term for taking or intercepting an active session between a client and server. There’s a number of ways this could be achieved making it worthy of it’s own article, however we will abbreviate for the sake of brevity.
Session Highjacking is typically achieved through the use of the acquisition of session keys, cookies or spoofing to gain access to a session. The reason for this is to bypass the authentication and authorisation checks made by the server which the attacker could not verify.
Session tokens can be compromised using the following methods:
- Cross-Site Scripting (XSS) – As mentioned in the XSS section the injection of malicious code into the users browser can result in the attacker gaining access to the session keys
- Side Jacking – Packet sniffers can be used to gain the session information from a user. This is typically done if the server resitrcts the user of SSL/TLS encryption for logon pages only.
- Session Fixation – Providing the client with a session key to spoof a user to accessing a compromised server
- Man-in the Middle attack – By spoofing the users access point an attacker can intercept the generated session token.
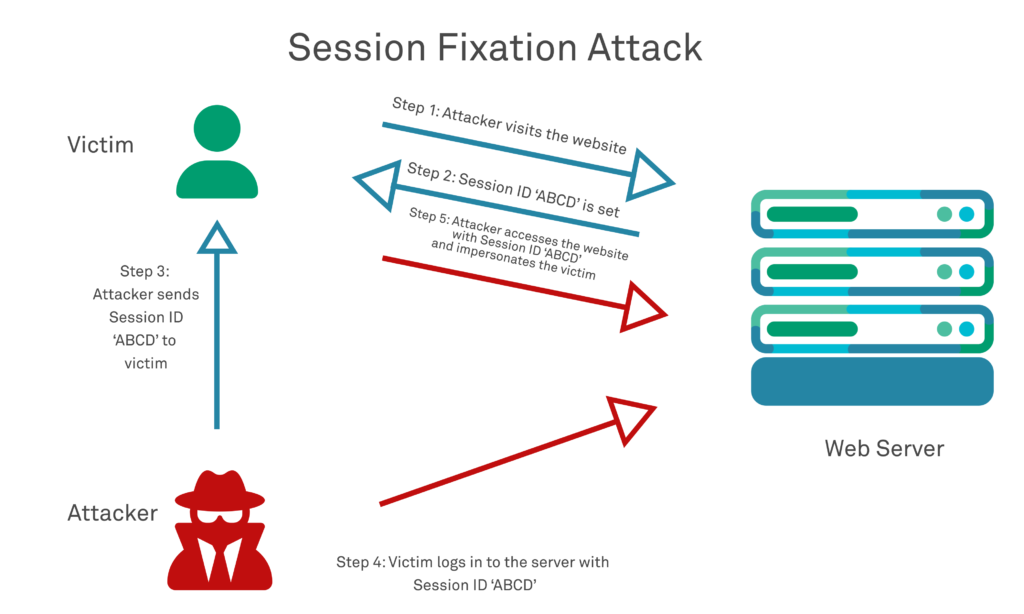
Safeguarding
- Enforce HTTPS – Make use of HTTPS to ensure the session is protected with SSL/TLS encryption
- HTTP only attribute – Setting the HTTPonly attribute tag to prevent XSS attacks from compromising the token
- Session Management – Regenerating Session key part session to limit impact in the case of a compromise
- Additional identity verification – Using additional verification such as IP, behavioural or geolocation can help prevent compromised session keys from being utilised
- VPN – Deploying a VPN will protect session traffic from snooping.
Conclusion
This provides a high level overview of the different form of web vulnerability attacks and how they can be exploited. There are many other vulnerability types which can be exploited such as the various authentication attacks, however the number of items on this prevent it from being practically includable within this article.
The attacks cover here are generally solvable and should be easily secured by a web professional, however without taking security into consideration it is easy to miss any of the above security methods needed to truly protect the server. Our saving grace however is that most of the methods are relatively easy to pick up using predefined rules within the SIEM.
References:
- XML External Entity (XXE) Processing | OWASP Foundation
- Cross Site Scripting (XSS) | OWASP Foundation
- Cross Site Scripting Prevention – OWASP Cheat Sheet Series
- SQL Injection (w3schools.com)
- SQL Stored Procedures (w3schools.com)
- What is directory traversal, and how to prevent it? | Web Security Academy (portswigger.net)
- Path Traversal | OWASP Foundation
- Session hijacking attack | OWASP Foundation
- What is Session Hijacking and How Do You Prevent It? – Blog | GlobalSign
- What is Session Hijacking & How Does It Work? | Venafi

