Windows System Processes – what they are and detecting malicious intrusion or fakes
I’m currently learning the ‘Core Windows Processes’ module on TryHackMe and a topic which stuck out to me is the detection and eradication of Malicious Windows Processes. For the examples used in this article I have used Process Hacker.
What is a malicious Windows process?
Commonly deployed as part of a root kit which compromises the kernel a malicious system process is a background process which can exploit it’s abused system privilege in a number of says such as acting as a APT, C&C, ransomware or providing a ledge for lateral movement.
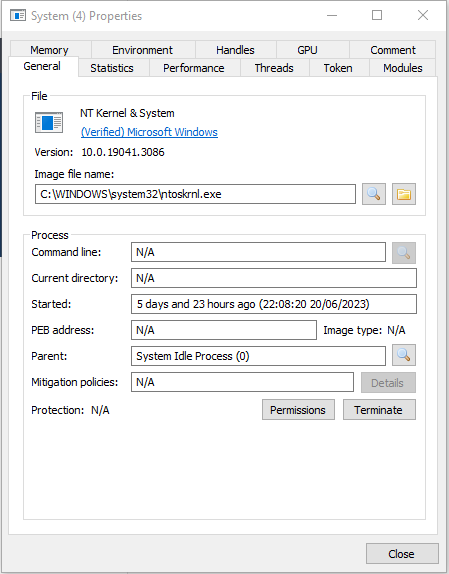
System.exe
The System thread is unique which runs in the kernel. This process primarily handles threads that run in system and Kernel NT memory.

While there are lot of variables here we need to be able to determine if these processes are real or fake. Some ways we can determine this are as follows:
- System Idle Process (0) is the only possible parent
- Multiple instances of the ‘System’ process
- PID different from 4
- Not running in Session 0
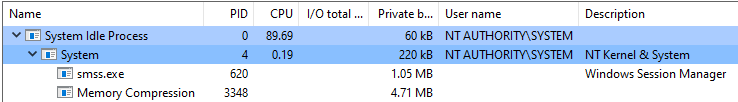
smss.exe
smss.exe is short for the Session Manager Subsystem. It is alternatively known as the Windows Session Manager and is responsible for the creation and management of new sessions.
This is a user-mode process and starts the follow up processes winlogon.exe and csrss.exe. It runs a number of functions including:
- Launching any subsystems specified in HKLM\System\CurrentControlSet\Control\Session Manager\Subsystems
- Creating enviromental variables
- Creating virtual memory paging files

Steps for detecting malicious versions includes:
- Variance in the image path which should be: %SystemRoot%\System32\smss.exe
- Parent process differing from System
- Multiple instances
- Alternative user account than Local System
It’s also worth being wary about the contents of the above mentioned registry entry for unauthorised additions.
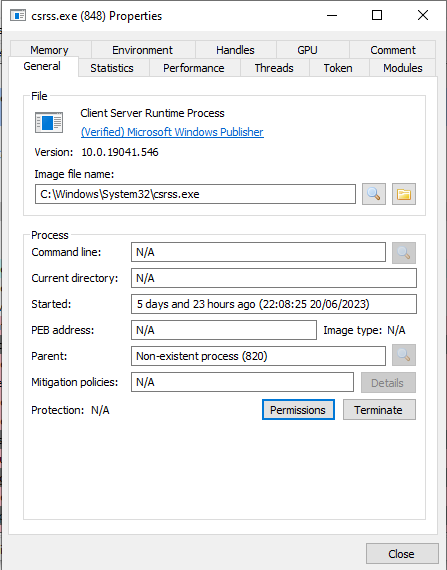
csrss.exe
The Client Server Runtime Process is another user-mode subsystem process. This is a persistent process and is required at all times. The process handles the Win32 console Window (cmd prompt and others) and threat creation/deletion.
This process additionally provides other applications access to Windows systems via an API allowing functions such as drive mapping and shutdowns.
Steps for detecting malicious versions includes:
- This must always have a parent process of some form
- A imagine path which differs from C:\Windows\System32
- A different user than ‘System’
An additional point worth noting is that attackers sometimes masquerade processes with a similar but slightly different spelling.
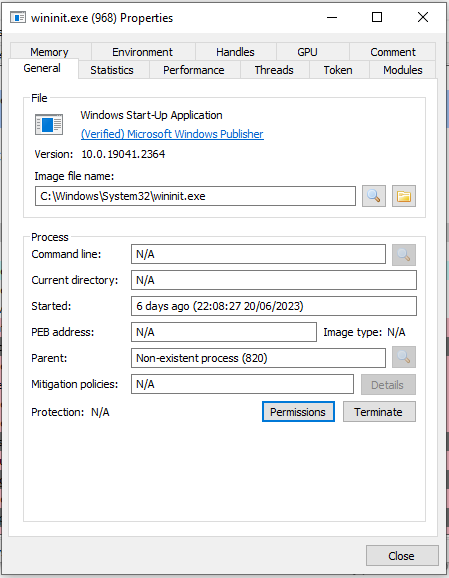
wininit.exe
Windows Initialization Process is a persistent System process which is responsible for the launching of services.exe, lsaas.exe and lsaiso.exe.
Steps for detecting malicious versions includes
- This must always have a parent process of some form
- A imagine path which differs from C:\Windows\System32
- A different user than ‘System’
- Multiple instances
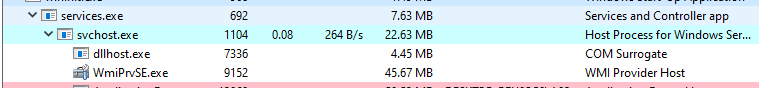
services.exe
A child service to wininit.exe, Services.exe is perhaps the most recognisable to fellow IT practitioners. This process handles the loading / starting /stopping services. For it’s data-table it references the registry table HKLM\System\CurrentControlSet\Services.
Services.exe is parent to several other processes including svchost.exe, msmpeng.exe, dllhost.exe.
Steps for detecting malicious versions includes
- Parent process which isn’t “wininit.exe”
- A imagine path which differs from C:\Windows\System32
- A different user than ‘System’
- Multiple instances
svchost.exe
Service Host is a child process which hosts running services. As mentioned previously it is a child process to services.exe
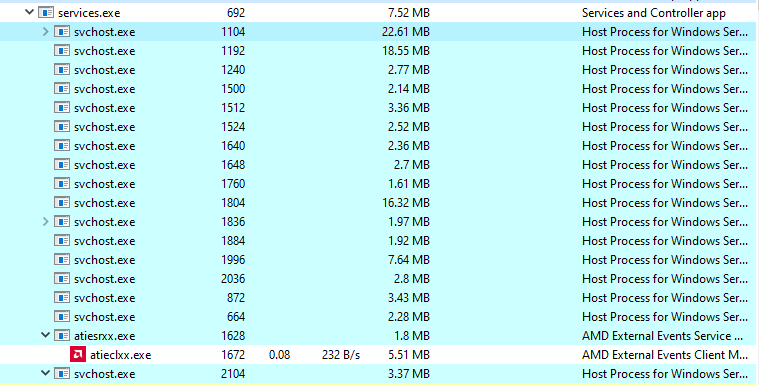
As this is not a unique process and can be launched at any time the PID number varies significantly.
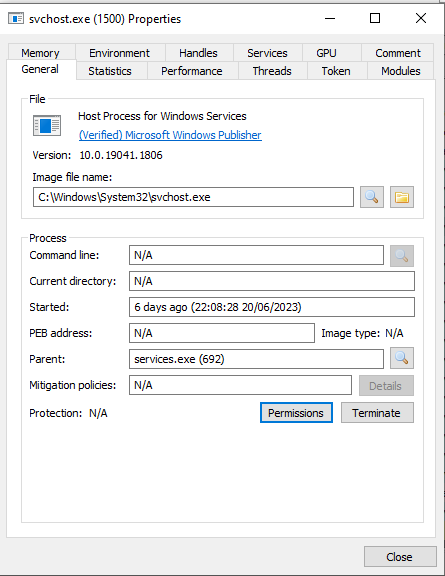
Steps for detecting malicious versions includes
- Parent process which isn’t “wininit.exe”
- A imagine path which differs from C:\Windows\System32
- The absence of the -K parameter
lsass.exe
Local Security Authority Subsystem Service (LSASS) is a Windows Process that enforces security policy on the machine. It handles a wide variety of security related Windows services including logon verification, password changes, access tokens. Actions made with involvement of LSASS are recorded to the Windows Security log.
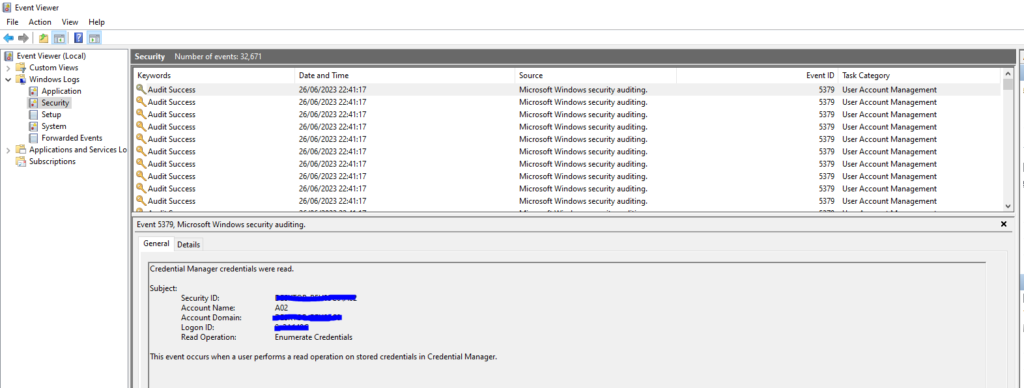
LSASS additionally creates security tokens for SAM, AD and NETLOGON. It utilises authentication packages in HKLM\System\CurrentControlSet\Control\Lsa
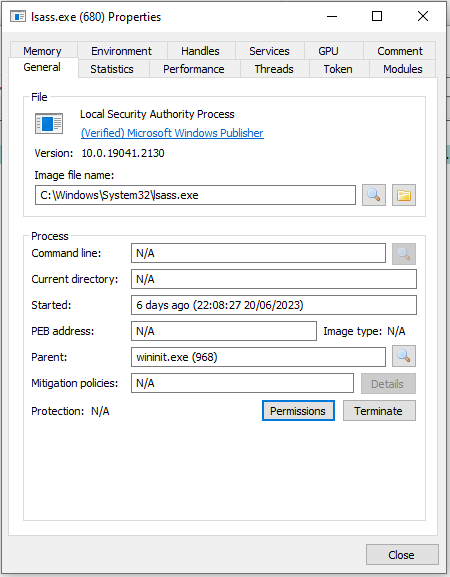
Steps for detecting malicious versions includes
- Parent process which isn’t “wininit.exe”
- A imagine path which differs from C:\Windows\System32
- Multiple running instances
- Not running as user ‘system’
This is a common target for attackers. More reading on this can be found here.
winlogon.exe
Windows Logon is a service which handles the Secure Attention Sequence (SAS). This is a system that handles a number of functions and is accessed via CTRL + ALT + DELETE.
While we typically use this to lock a screen it can also execute task manager, change a password, perform shutdowns and log users out.
This function is used by NT and protects against Trojan Horse applications as the SAS is incapable of executing any other programmes meaning the hotkey will remain uncorrupted. It also provides protection against logon scripts which limits access to the OS.
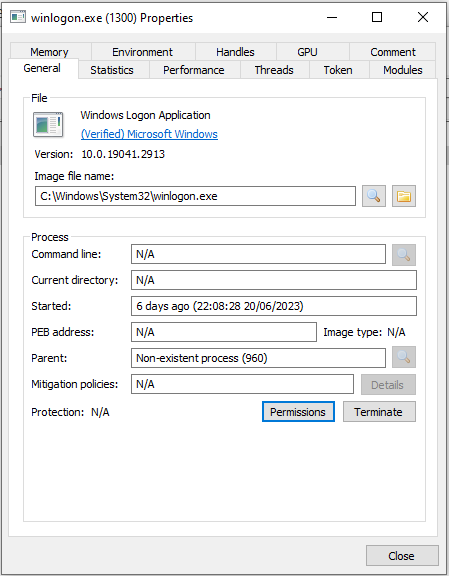
Steps for detecting malicious versions includes
- A missing parent process of any sort
- A imagine path which differs from C:\Windows\System32
- Multiple running instances
- Not running as user ‘system’
explorer.exe
Along with services Windows Explorer is likely the most well known of what we’ve covered in this article. Responsible for providing the end user with a navigation UI to access files and folders it’s an essential function for the majority of users.
This process also handles other graphical functions such as the start and task bars. The parent of Windows Explorer is executed by the ephemeral process userinit.exe.

Steps for detecting malicious versions includes
- If a parent process is there. This is executed by userinit which exits after.
- A imagine path which differs from C:\Windows\System32
- Multiple running instances
- Running as an unknown user
Additional reading referenced for this post:
- https://en.wikipedia.org/wiki/Windows_Console
- https://learn.microsoft.com/en-us/windows-hardware/drivers/gettingstarted/user-mode-and-kernel-mode
- https://medium.com/chingu/an-introduction-to-environment-variables-and-how-to-use-them-f602f66d15fa#:~:text=An%20environment%20variable%20is%20a,at%20a%20point%20in%20time.
- https://en.wikipedia.org/wiki/Architecture_of_Windows_NT
- https://nasbench.medium.com/windows-system-processes-an-overview-for-blue-teams-42fa7a617920
- https://www.techtarget.com/searchenterprisedesktop/definition/Security-Accounts-Manager#:~:text=The%20Security%20Accounts%20Manager%20(SAM)%20is%20a%20database%20file%20in,case%20the%20system%20is%20stolen.
- https://networkencyclopedia.com/secure-attention-sequence-sas/
- https://www.threathunting.se/tag/windows-process/
- https://www.sans.org/security-resources/posters/hunt-evil/165/download
- https://docs.microsoft.com/en-us/sysinternals/resources/windows-internals